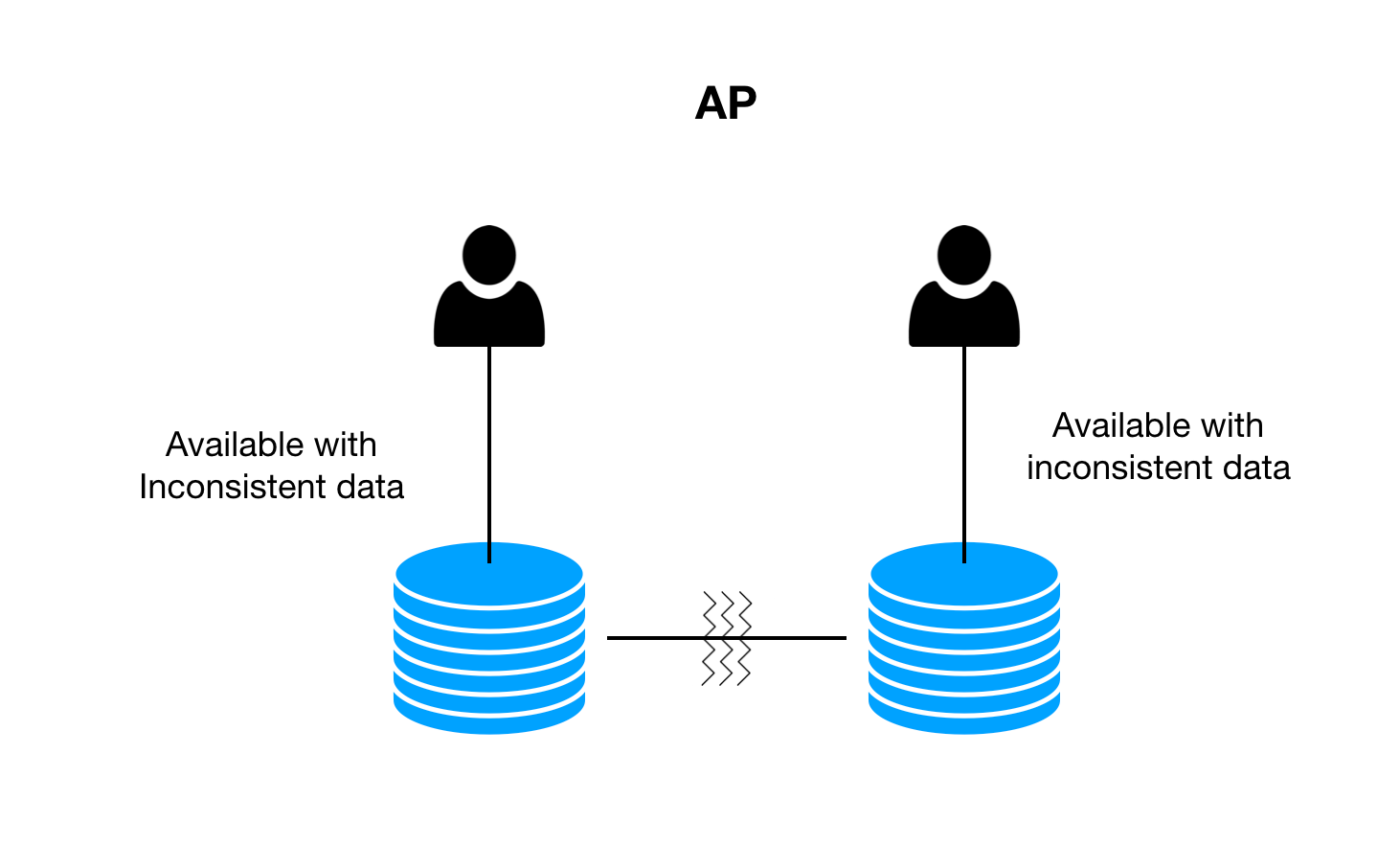
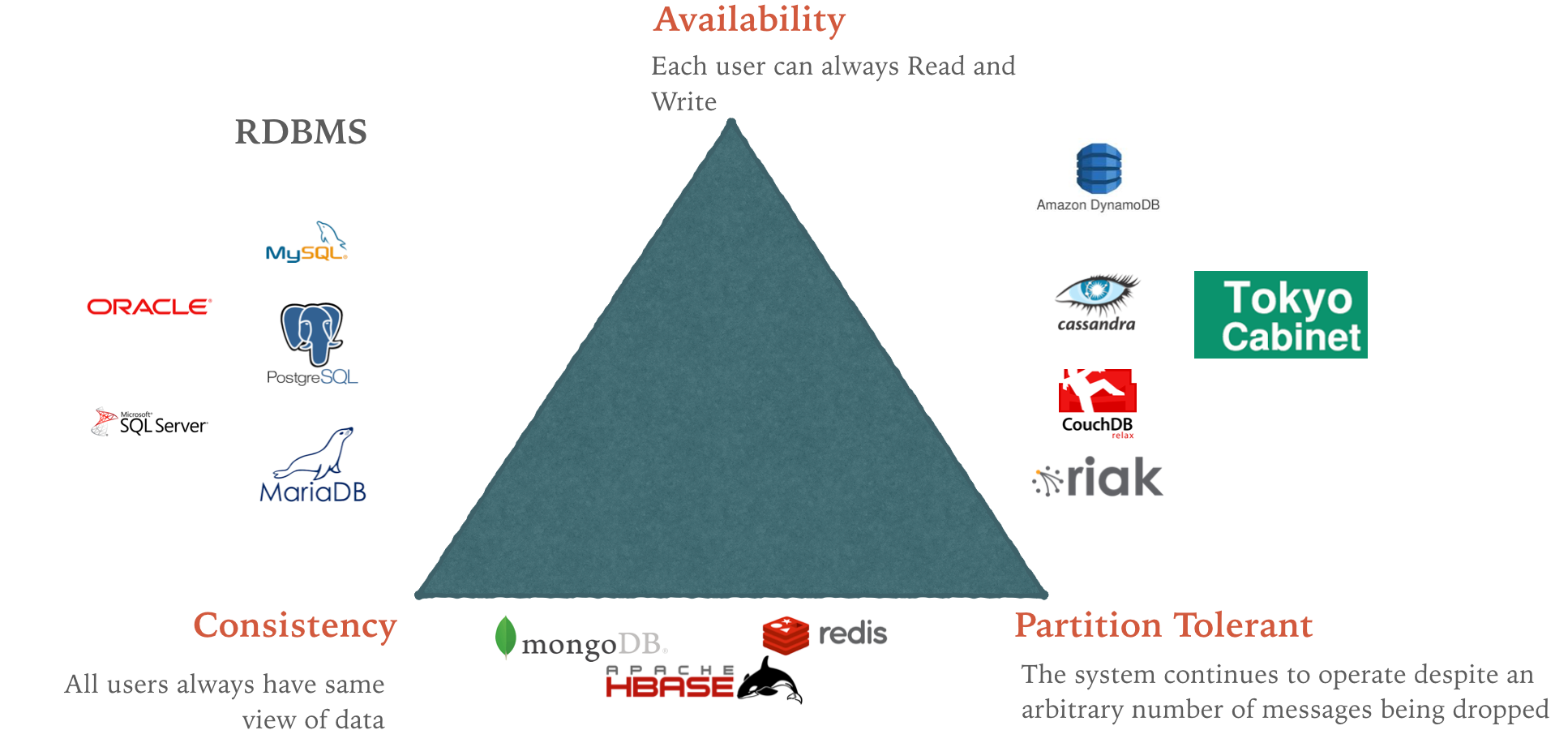
Steps of Spring Security and JWT:
1. Dependency of jsonWebToken in Maven.
2. In Main class, @EnableWebSecurity annotation which extends WebSecurityConfigurerAdapter
3. Override configure method
protected void configure(HttpSecurity httpSecurity){
httpSecurity.csrf().disable()
.authorizeRequests().antMatchers("/authenticate")
.permitAll()
.anyRequest().authenticated().and().
.exceptionHandling().and().sessionManagement()
.sessionCreationPolicy(SessionCreationPolicy.STATELESS);
httSecurity.addFIlterBefore(jwtRequestFilter, userNamePwdAuthenticationFIlter);
4. Make request Mapping of "/authenticate" where jwtTokenUtil.generateToken(userDetails).
5. Create a Service class jwtTokenUtil having generateToken method:
JwtBuilder.setClaims(claims).setSubject(subject).setIssuedAt(time).setExpiration(time)
.signWith(SignatureAlgorithm.H256, SECRET_KEY).compare()
6. also validateToken by extracting userName.
7. Create Filter JwtRequestFilter extends OncePerRequestFilter
@Override
protected void doFilterInternal(HttpServletRequest request, response, filterChain){
final String auth = request.getHeader("Authorization");
jwtUtil.extractUserName(auth);
8. validateToken
9. chain.doFilter(request, response);